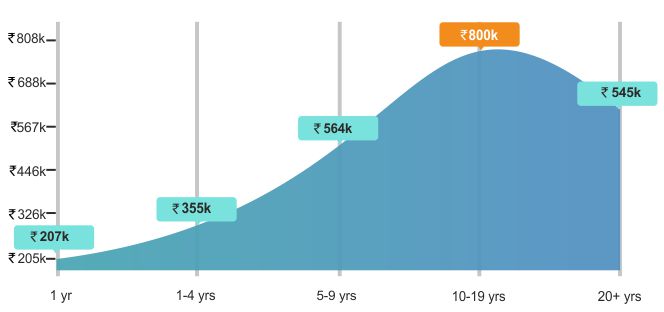
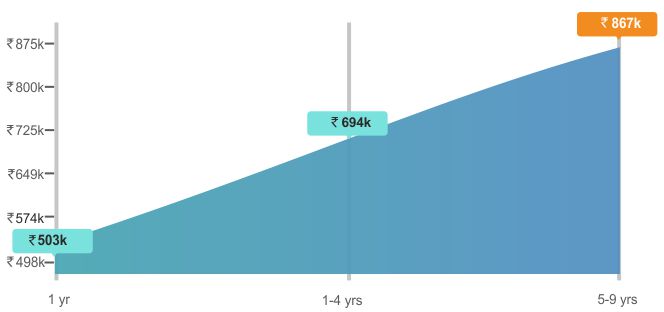
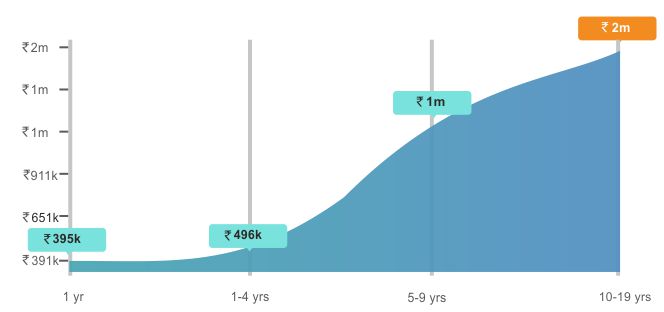
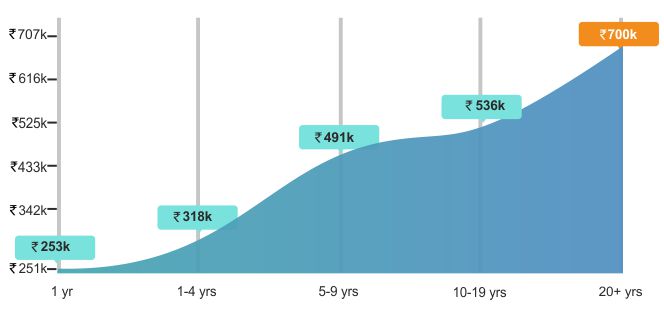
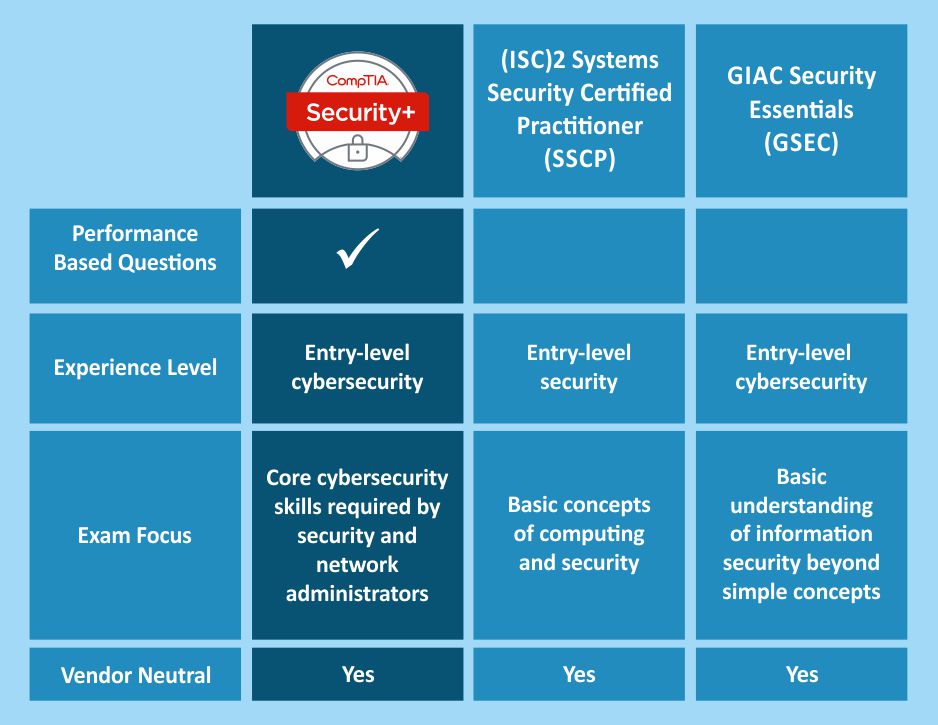
Attaining the security plus certification validates a professional having core security skills to protect networking devices, servers, and cloud operations from unauthorized access. Mildain’s top-rated instructors, deployed across nations, provide real-industry lab assignments to transform professionals from problem solvers experts to masters.
- Course is developed for IT professionals
- Knowledge enhancement on TCP, and TCP/IP networking
- Administrating Window-based networks
- It is a next-level course specially developed for already working IT professionals.
Also, the participants must have a basic knowledge of other operating systems such as macOS, Unix, or Linux. This course is for the professionals who want to pursue a career further in IT by attaining foundational knowledge of security subjects.
How Security+ course developed?
A team of instructors was incorporated in the development of the security+ curriculum. The curriculum was developed after taking feedback, having thorough group discussions, reviews, and surveys. The result that was derived is a suite of resources addressing entire security challenges faced by the security professionals in a domain. The course included several lab assignments equipping students to practice what they are learning using real, hands-on experiences on the live networks.
Result of Security+
The certified professionals are known as specialists in resolving every security issue in the domain. These IT security experts have in-depth knowledge of core technologies applied and used in networks and systems today. For instance, the planning, installing, and implementing security solutions in cloud management or computing technology are considered in CompTIA security plus. Today, it has turned out to be an industry-standard needed to pursue further a successful career in IT security in today’s digital world.
Why choose Mildain for Security+ Certification?
- Mildain Solutions is a partner to CompTIA and EC-Council in IT training.
- The training partner has created various IT training courses and programs
- Entire courses developed assist professionals to enhance their network security skills.
- Courses validates quick and cost-effective solutions
- Top-rated instructor imparting real-industry knowledge
This course certifies the trending skills needed by present-day IT support specialists. Global enterprises and vendors have acknowledged security+. The endorsement confirms that a certified applicant is capable of managing and eliminating attacks, threats, and vulnerabilities in cyberspace.
Also, it covers the technical areas in network architecture and designing. Security+ certification training explains the vital need for security concepts in an enterprise environment. It also summarizes the virtualization, cloud computing, secure application development, deployment, and automation concepts. Along with it, the professionals learn about authentication and authorization design, the basics of cryptographic concepts.
Career prospects in Security+ Certification
This CompTIA security plus confirms that the right applicants have the right skills to develop in an IT career. The course includes skills vital to support a business’s needs. By awarding the certification choices for precise job scenarios, the certification provides the capability to increase their careers in a sure space, and employers the flexibility to choose the exam courses that best fit their desires.
Candidates earning the qualifications obtain the knowledge and skills to protect the network from hackers and other unauthorized accesses. It enhances the capability to describe the features and functions integrated into networking components. The components contain comparison, analysis, implementation, and deploying techniques to manage different networks.
CompTIA Security+ Jobs
In the present scenario, the requirement for skilled security plus support professionals is endlessly growing, and it is happening to be an appreciated credential to launch or boost a new career. There is a long list of international organizations searching for security professionals capable of performing and managing IT security and network support.
The certification focuses on technical areas such as attacks, threats, vulnerabilities, architecture, design, implementation, operations, incident response, governance, risk, and compliance. Candidates who have attained in-depth knowledge in all the topics, and completed entire lab sessions receive a high-end position in the IT industry.
Because of the cumulative receiving of enterprise-ready platforms, mutually employees and professionals comprehend the meaning of skilled validation. The industry identifies that certification is a noble entity imparting in everyday security management systems.
Security+ exam Cost
It can be skilled swiftly and cost-effectively. There are no fundamentals required to opt for the training certification. The training led by top-rated instructors informs the skills required to broad projects on time and within budget. We all identify that the need for skilled technology participants with knowledge in meeting technology withstands growing, as more industries accept digital Solutions. The security plus certification is a valuable credential to expand a career with growing technology.
Security+ is an important security certification that a participant must achieve. It creates the core knowledge needed for any cybersecurity role and delivers a springboard to intermediate-level security jobs.
The course incorporates best practices in hands-on troubleshooting, problem-solving skills, and implement appropriate security solutions comprising monitoring and securing hybrid environments.