CompTIA Cysa+ Certification Training
Exam Code CS0-002
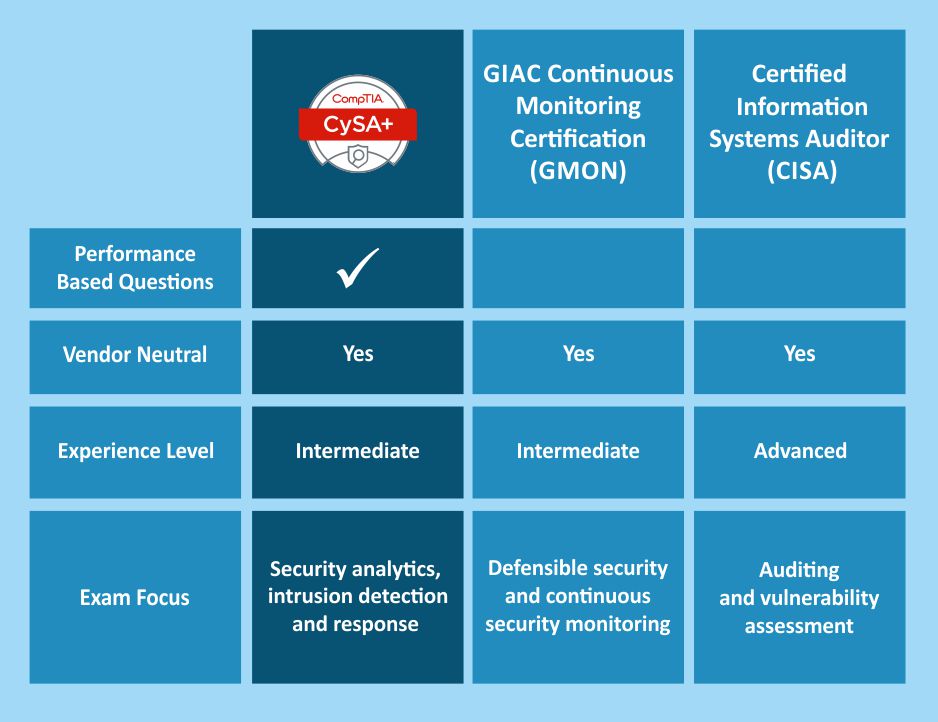
CompTIA Cybersecurity Analyst certification educates participants about the behavioral analytics of the networks and devices to check, identify, and combat cybersecurity threats.
- 40 Hours Instructor led Online Training
- Authorized Digital Learning Materials
- Lifetime Free Content Access
- Flexible Schedule Learn Anytime, Anywhere.
- Training Completion Certificate
- 24x7 After Course Support
Accreditation with